Solar cybersecurity vulnerabilities: 6 ways in which hackers target solar installations
In this article, we explain what is at risk when solar cybersecurity vulnerabilities are exploited successfully. We also show you how hackers are able to target solar installations.

A few years ago, the state-run Radiocommunication Agency Netherlands launched an investigation into whether PV inverters pose a threat to the cybersecurity of the Dutch electricity system.
A Dutch hacker found out they could access PV systems operated via a monitoring tool made by Chinese manufacturer, Solarman. This hacker was able to access Dutch customers’ private data, create new customer accounts and delete existing users.
The hacker was also able to find out how much electricity specific solar panels generated and managed to download, adjust and upload inverter firmware. We don’t need to explain that this poses very, very serious security risks.
As the solar energy business booms, security risks rise
This happened in 2022, mind you. At the time of writing, in October 2024, the solar energy business is still booming. And with it, security risks like the hack mentioned above, boom too.
The question, then, should be: are businesses in the utilities industry prepared to prevent and solve cyberattacks? A 2022 survey by Ericsson reported:
“62% of respondents within utilities either do not know or do not believe they have the skills and tools in their organizations to protect against cyber threats.”
The state of solar cybersecurity was vulnerable then, and while security breach cases like the one involving the Dutch radio service have raised some awareness, we’re not there yet.
Luckily, the EU has introduced regulatory changes that will help expedite its member states to take issues like these more seriously. The NIS2 (“Network and Information Security”) directive came into effect in January 2023. Member states have until October 17, 2024 to turn this directive into national law.

This directive aims to “enhance the security of network and information systems within the EU by requiring operators of critical infrastructure and essential services to implement appropriate security measures and report any incidents to the relevant authorities.”
It’s a good start, but one of the most urgent challenges for countries and utilities businesses trying to implement NIS2 is the severe shortage of qualified cybersecurity specialists in the industry.
In May of 2024, the utilities sector reported a rise from 36% to 54% in regards to the shortage of cybersecurity specialists in the Netherlands. With the NIS2 directive coming into full effect in October, we predict this number to keep increasing.
Bearing this shortage of specialists in mind, the utilities and solar industries are going to be increasingly dependent on companies like Helin to ensure their data, interfaces and applications are safe, secure and encrypted.
What’s at risk when cyberattacks on solar succeed
Before we show you how hackers are able to target solar installations, let’s quickly explain what is at risk when solar cybersecurity vulnerabilities are exploited successfully.
The consequences can be significant, starting with the disruption of the power supply. Successful hacks can lead to solar farms and grids experiencing instability, causing interruptions in energy generation and supply. This, in turn, can lead to blackouts or limited access to electricity for businesses and households.
Besides, disruptions can have a cascading effect, impacting other sectors that rely on consistent power, such as healthcare, communications, and transportation. To put that into perspective, one expert mentioned hackers would only need to take control of 3 gigawatts of capacity to disrupt the entire European grid.
The economic consequences of successful cyberattacks are equally severe. Solar companies face financial losses due to halted operations, expensive repairs, and the potential loss of intellectual property (IP).
Even more market volatility could follow, as confidence in renewable energy sources might diminish, leading to increased reliance on fossil fuels. This shift can have an environmental impact, as it undermines efforts to transition to cleaner energy.
These attacks expose vulnerabilities in national security, particularly when critical infrastructure is affected, leaving countries at risk of further manipulation of their energy markets.
Lastly, successful cyberattacks can result in data breaches, compromising sensitive information and potentially leading to the loss of proprietary technology and innovation.
The cumulative effect of these consequences not only threatens the growth of renewable energy but also destabilizes energy markets and creates long-term national security concerns.
Needless to say, the consequences of doing nothing to fix cybersecurity vulnerabilities in solar are extremely severe.
6 ways in which hackers can target solar installations
To better help you understand how hackers target solar installations, we’ve listed 6 of the most common ways in which they do so, below.
1. Inverter attacks
PV inverters are often directly connected to the internet through an API, for monitoring and remote management. These setups usually don’t have the best security.
An attack by hackers typically starts when vulnerabilities in the inverter's firmware or connection to the internet are exploited. For example, a firmware update could leave an internet port open permanently, exposing the system.
Hackers can easily get in through open ports, especially if the system’s still using default passwords. Once inside, they can take control of the inverter and manipulate the system, for instance by disrupting communication and cloud functions, requiring manual fixes or sometimes even complete replacement of the inverters.
2. SCADA attacks
SCADA systems used in solar installations can be vulnerable. They’re easy targets since they’re designed to be more user-friendly than secure.
Originally built to control infrastructure like power grids and pipelines, SCADA systems have transitioned from proprietary, isolated systems to more connected networks, increasing their exposure to cyber threats.
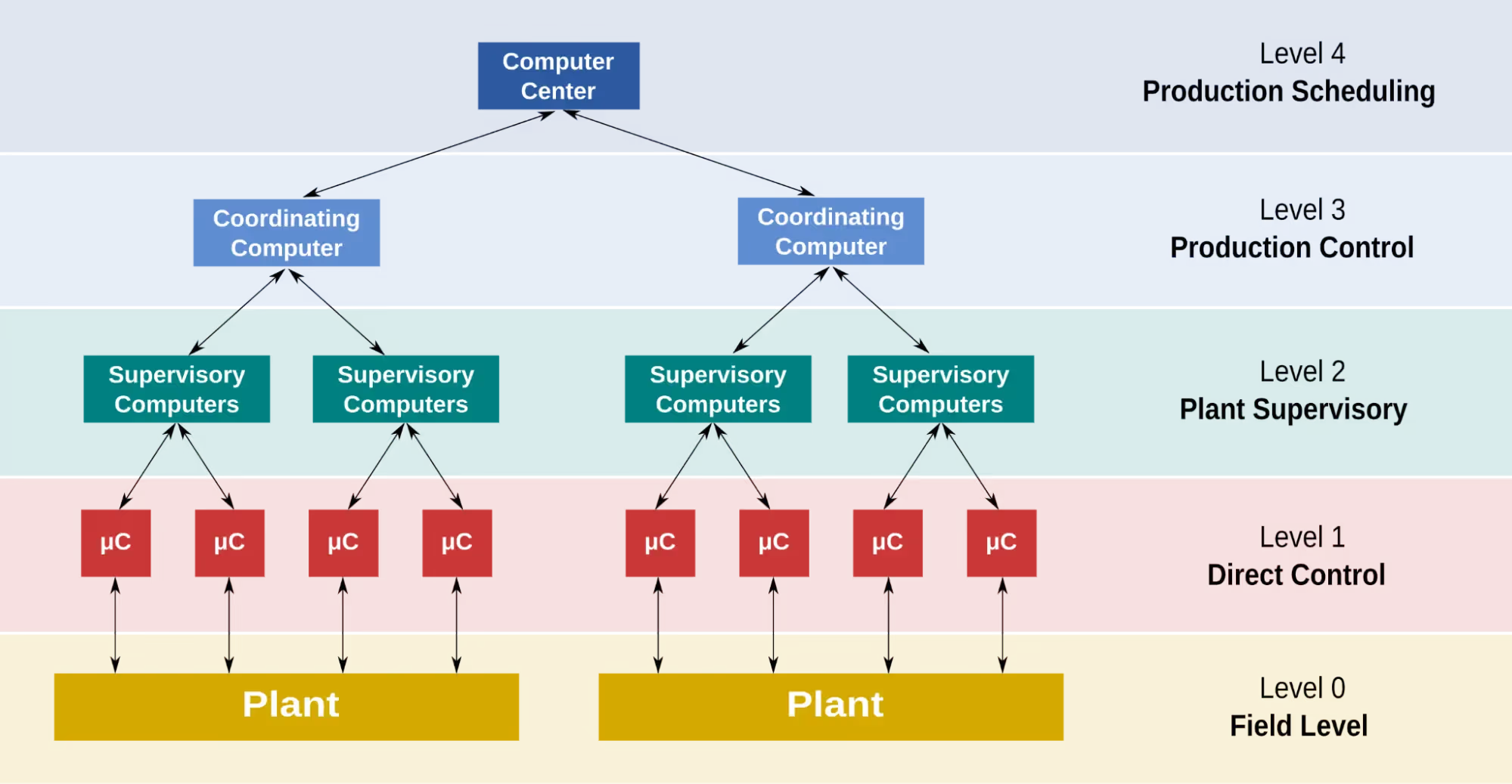
Attackers can exploit weak authentication, outdated software, and unsecured communication channels to gain unauthorized access. Once inside, hackers can manipulate control software, inject false data, or even disable critical functions.
3. Network (LAN/WAN) attacks
Hackers can also target solar installations through network (LAN/WAN) attacks by exploiting open ports, introducing malware or ransomware, and intercepting unencrypted communication.
Open ports give unauthorized access, malware can disrupt operations or demand ransom, and unencrypted channels allow attackers to manipulate data or steal sensitive information. To keep these networks safe, you need solid firewalls, encryption, and regular updates.
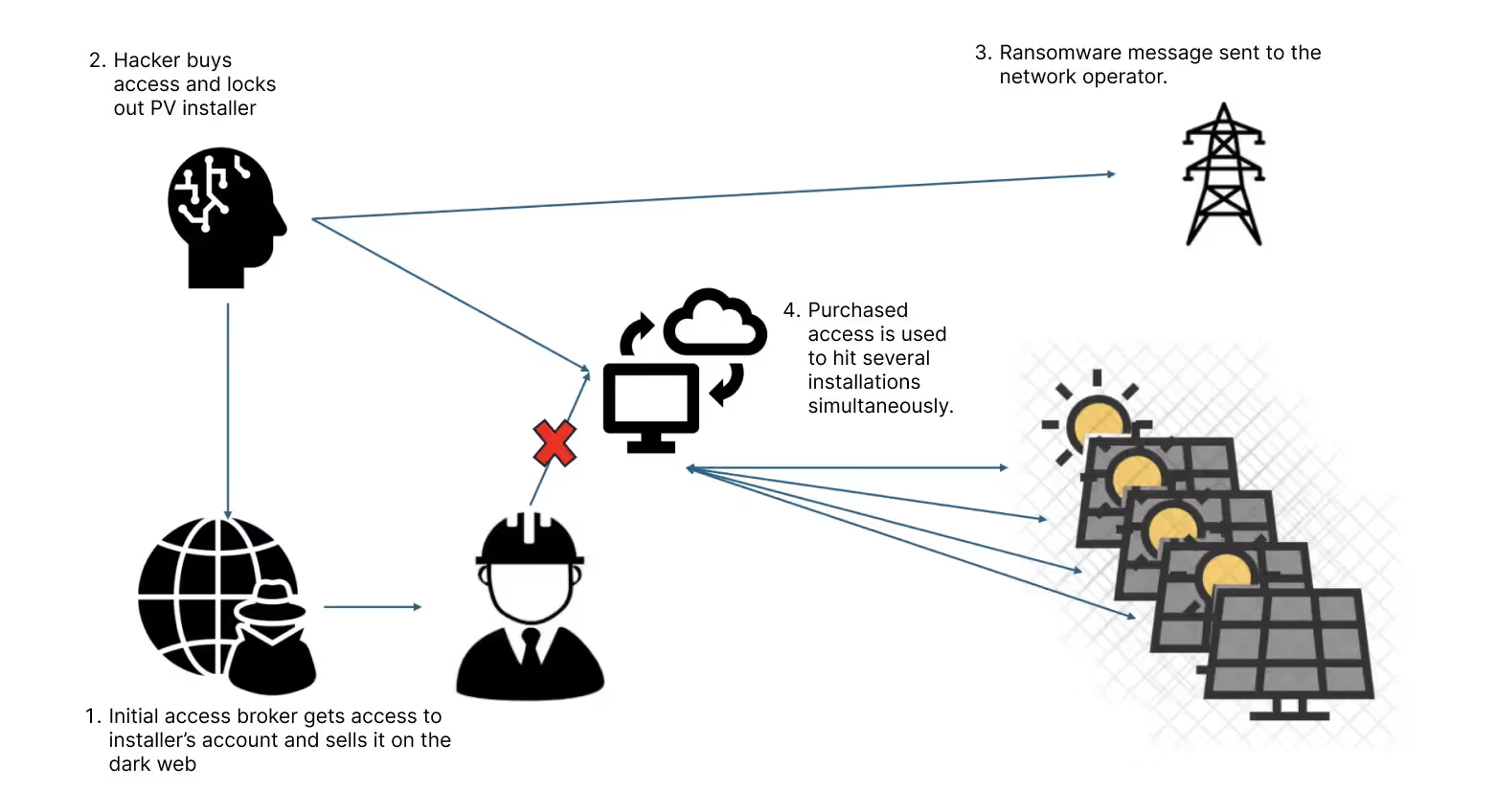
4. Cloud-based attacks
Hackers can target solar installations through cloud-based attacks by exploiting login credentials and intercepting communications via man-in-the-middle (MITM) attacks.
In a cloud-based environment, where solar installations rely on cloud platforms for remote monitoring and data storage, weak or compromised login credentials can give hackers direct access to sensitive systems. Once they gain entry, attackers can alter configurations or access data.
In MITM attacks, hackers intercept communications between the solar installation and the cloud platform. By doing so, they can modify transmitted data, inject malicious commands, or steal confidential information without being detected.
It’s crucial to secure cloud-based systems in solar energy with strong passwords, two-factor authentication, and encryption.
5. Energy Management Systems (EMS) attacks
Hackers can also target Energy Management Systems (EMS) by exploiting weak or compromised login credentials.
These systems, which keep track of and control energy consumption in power grids and industrial facilities, can often be accessed remotely. If attackers gain access to login credentials, either through phishing, brute force, or exploiting weak password security, they can get unauthorized access to the EMS.
Once inside, hackers can manipulate energy distribution, disrupt power flows, or steal sensitive data related to energy consumption patterns. This can cause operational failures, energy loss, or even trigger cascading effects across connected systems.
Using multi-factor authentication and regularly updating credentials is key to keeping these EMS systems safe.
6. 3rd-party service provider attacks
Lastly, hackers can target solar installations through third-party service provider attacks by exploiting weaknesses in the security of vendors and service providers that support the solar systems.
If these third-party vendors do not maintain robust security protocols, they can become a point of entry for attackers. Hackers may breach the vendor’s systems and, from there, access the solar installation’s network, often bypassing more direct security measures.
These attacks show the importance of thorough vendor assessments and ensuring that third-party providers follow strict security practices.
Use Helin’s edge intelligence platform to avoid solar cybersecurity vulnerabilities
When you implement a system like Helin’s edge intelligence platform for the renewable energy industry, you immediately avoid a whole bunch of cybersecurity vulnerabilities.
Helin combines a Public Key Infrastructure (PKI) to encrypt data offloading with application containers for secure devices. It uses node security logging based on the Prometheus data model. Through multi-modal security, you can encrypt your data offloading, updates, interfaces, and applications.
Let’s give you a better idea of the technical specifics of Helin’s security measures. These take place on three different layers:
- Edge / Node security (local): PKI, TPM 2.0, Prometheus data module
- Stream security: Encryption of data offloading via HTTPS, Encryption of updates & configuration secured by X.509 certificates and TLS, Encryption of local interfaces to (3rd-party) apps, with X.509 and TLS
- Cloud security: Continuous monitoring and threat detection, edge security monitoring, multi-tenant deployment
Want to learn more about what Helin’s edge intelligence platform can do to help you avoid solar cybersecurity vulnerabilities? Make sure to get in touch with one of our experts to discuss what this could mean for your business.
Want to read more?
Stay up to date with the latest trends and developments on the topic of industrial edge computing, monitoring and intelligence.
Get real-time insights
into your remote assets
Combine local artificial intelligence with a centrally managed data infrastructure for more accuracy, reduced congestion on your network and lower costs.